Students and faculty from 18 university-based cybersecurity clinics convened virtually to network and learn about the student-led Cyber Clinic at the University of Nevada Las Vegas
On April 18, the Consortium of Cybersecurity Clinics hosted its Spring 2024 “Clinic of Clinics”, a semesterly virtual event for students participating in cybersecurity clinics around the country to network, learn from experts in the field, and partake in group activities. This spring, 70 students from 18 different universities participated.
The event kicked off with a warm welcome from Ann Cleaveland, the Center for Long-Term Cybersecurity’s (CLTC) Executive Director, and Sarah Powazek, Director of CLTC’s Public Interest Cybersecurity Initiative. Both congratulated the Consortium on its recent growth.
Students then seized the opportunity to get better acquainted and network, grouping into breakout rooms to connect and learn more about the work being accomplished by their colleagues at other clinics. Attendees later regrouped to watch a presentation from the University of Nevada, Las Vegas’ (UNLV) Cyber Clinic, who showcased some internal tools and a training simulation students developed to teach new members.
Mathew Salcedo and Angel Garcia, two co-founders of UNLV’s Cyber Clinic, explained how their clinic specializes in providing free cybersecurity services to small local businesses in the Las Vegas valley.
The vast majority of clinics in the Consortium are faculty-led and taught as a semester-long course. UNLV’s Cyber Clinic is unique in that it operates as a student-led club, with support from faculty advisors, and operates year-round. This arrangement enables Cyber Clinic members to provide services to clients on an at-need basis, gives students more opportunities to gain experience working with different clients, and builds their skills over the course of their academic careers.
Salcedo and Garcia showcased the web portal application they created for their clinic. The portal is one of many internal tools their students have developed for Cyber Clinic, which serves to streamline clinic operations.
“Most of UNLV’s members have backgrounds in computer science, information systems, and cybersecurity. Many have an interest in software development,” said Salcedo. “This project allowed for some of our members to practice their programming and software development skills. Web applications are a very big portion of cybersecurity. In the past, members have been able to conduct penetration assessments or tests on our own website, too.”
Garcia explained to the audience how UNLV clinic students access the portal using an email and password, landing at a central dashboard that hosts a timesheet application for members to track their volunteering hours working on cases for clients. The dashboard also featured a training library, where students can access and track completed cybersecurity certification training– including student-developed training and the CompTIA Security+ certification.
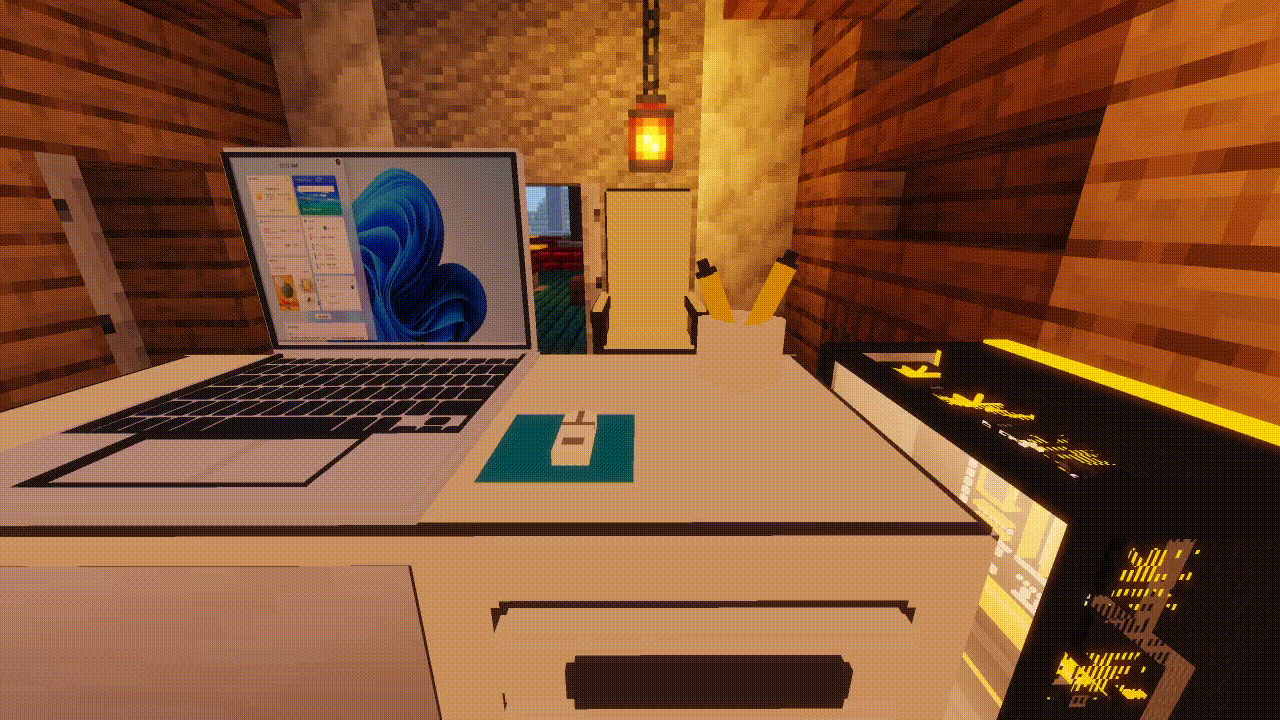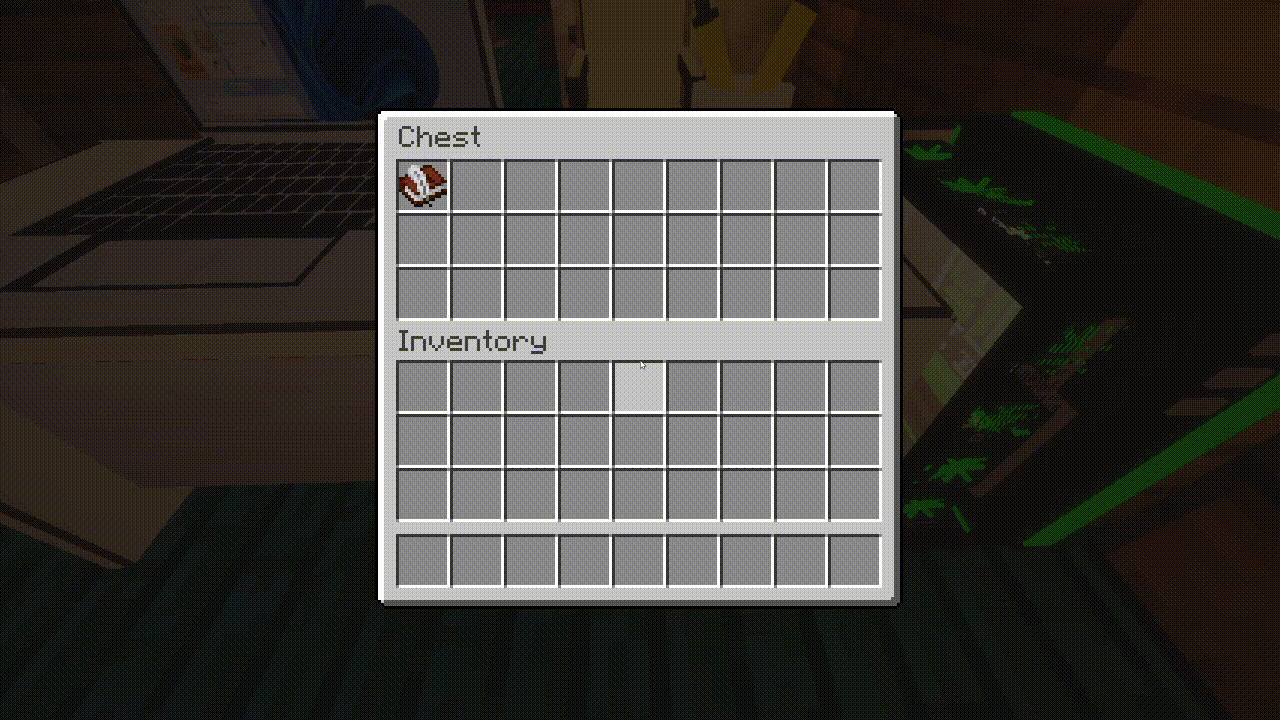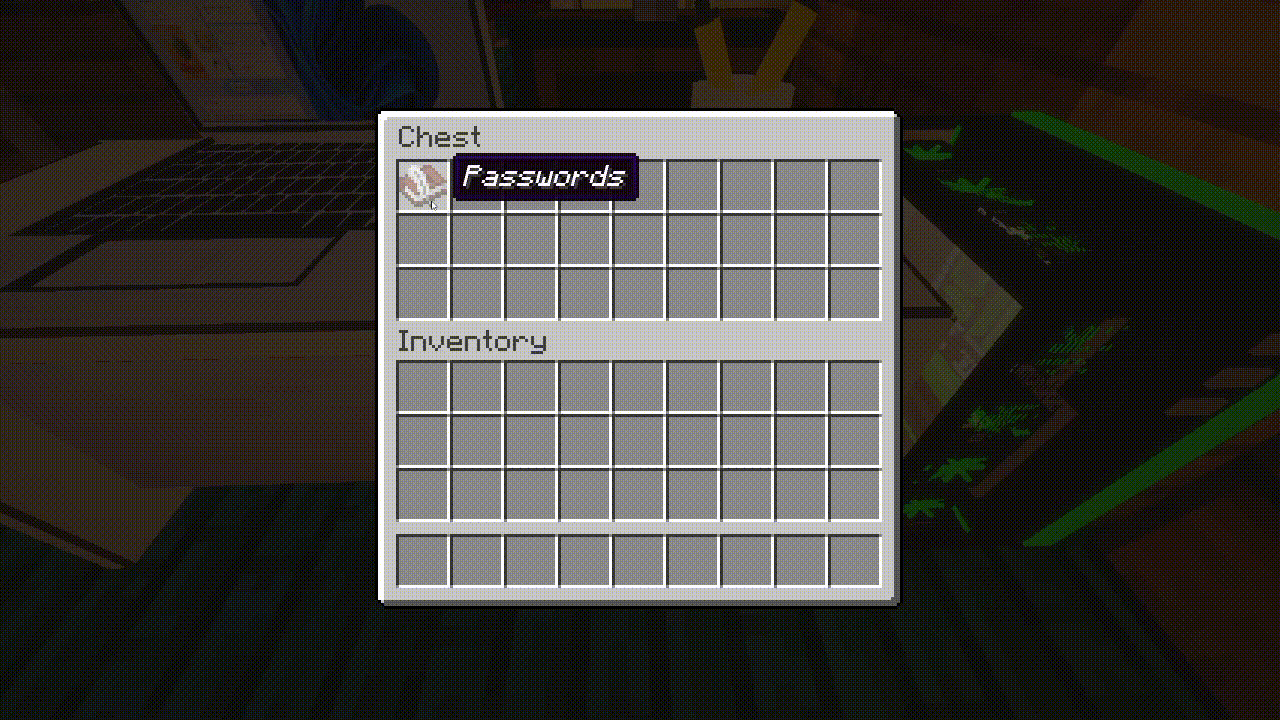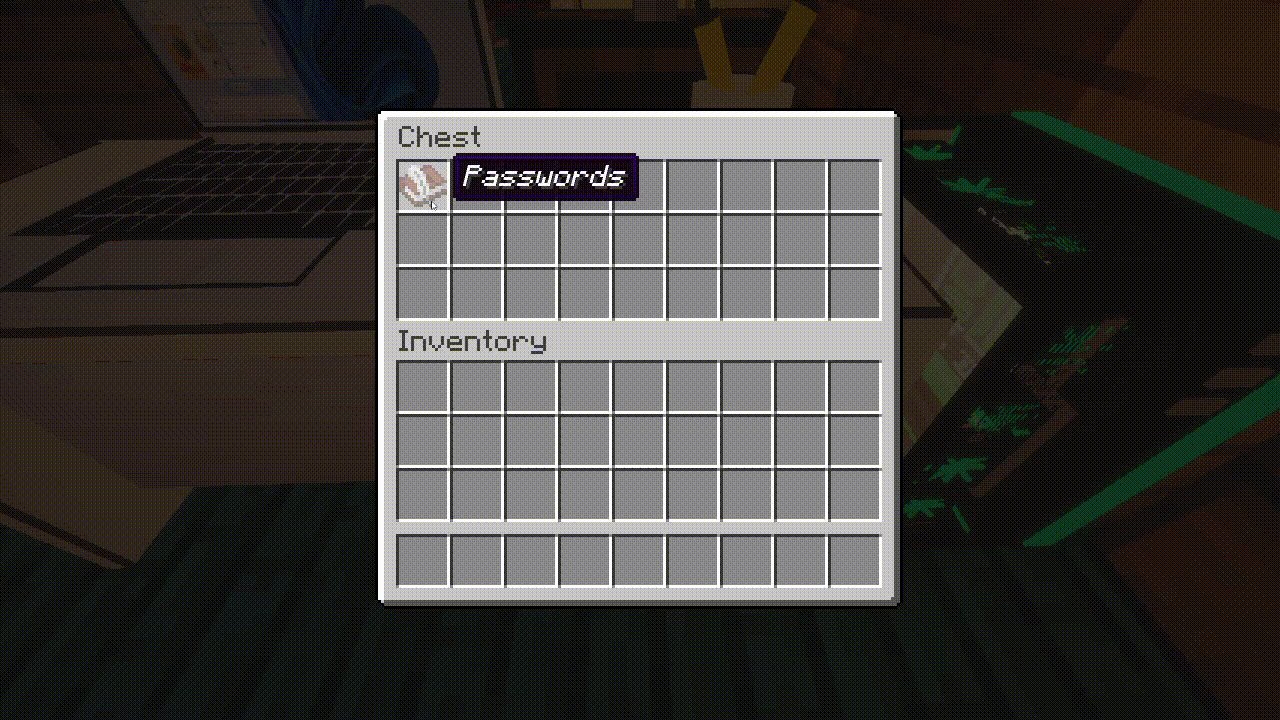
UNLV also shared their innovative approach to onboarding their clinic’s new members. Cyber Clinic’s leadership built a training simulation in Minecraft to prepare new members for conducting client site visits and train students how to identify cyber and operational risks in small businesses. At the “Clinic of Clinics” event, Salcedo and Garcia demoed a gameplay walkthrough of their Minecraft simulation, which was modeled after the Krusty Krab restaurant from the Spongebob Squarepants television show.
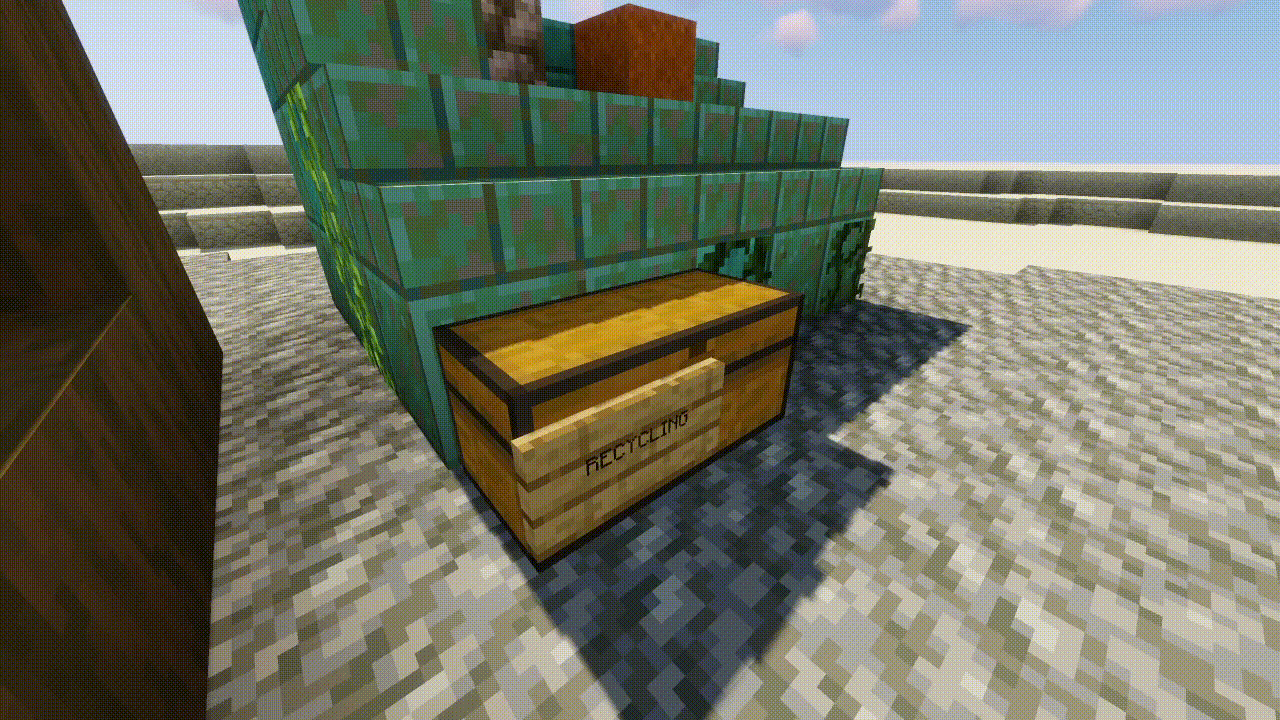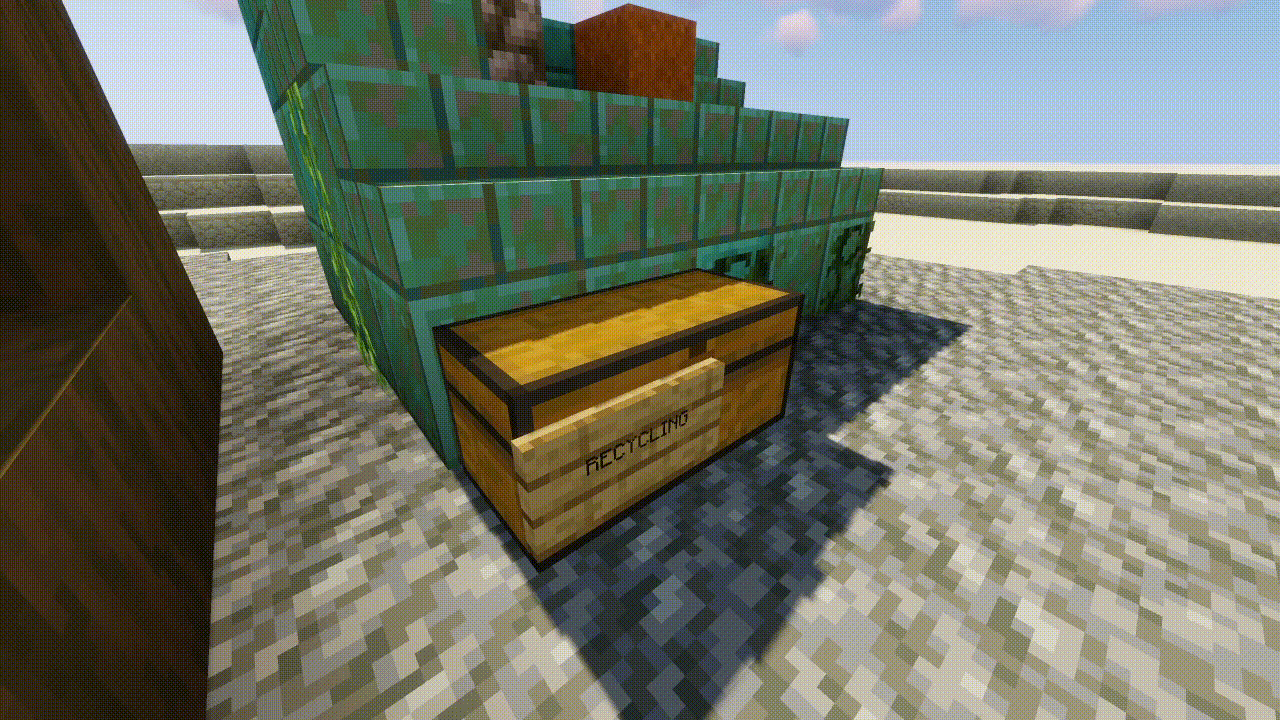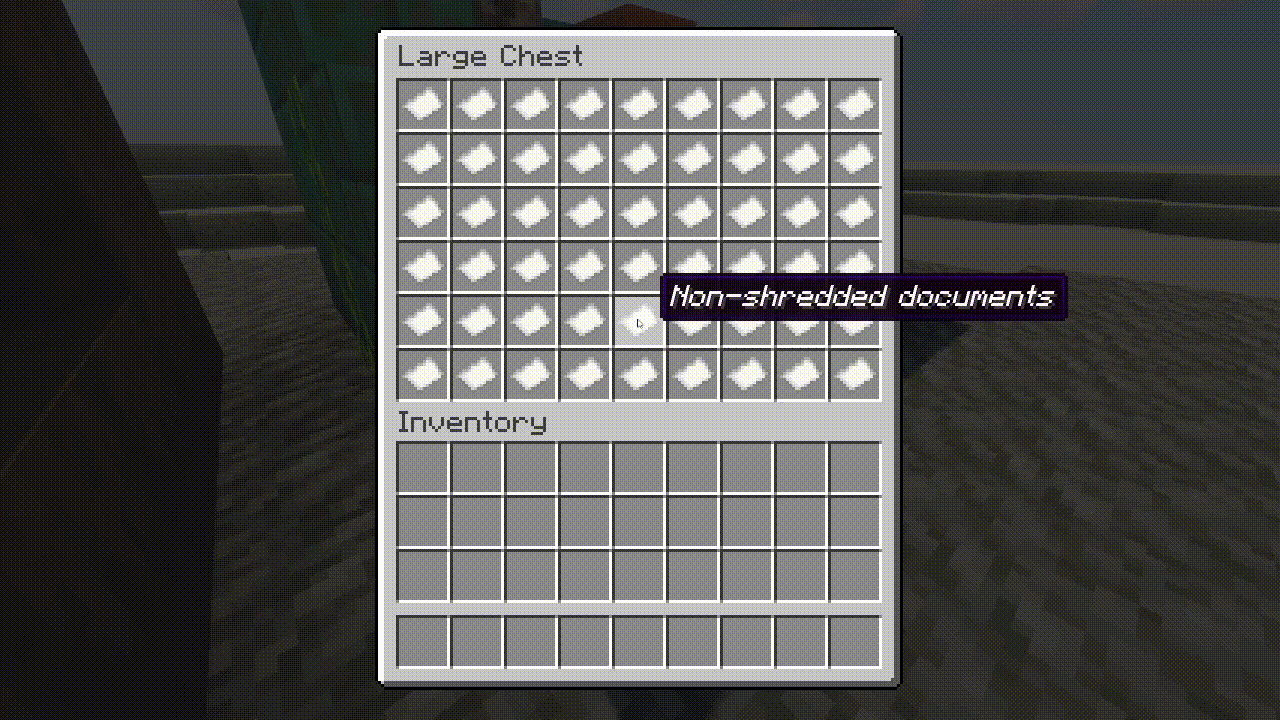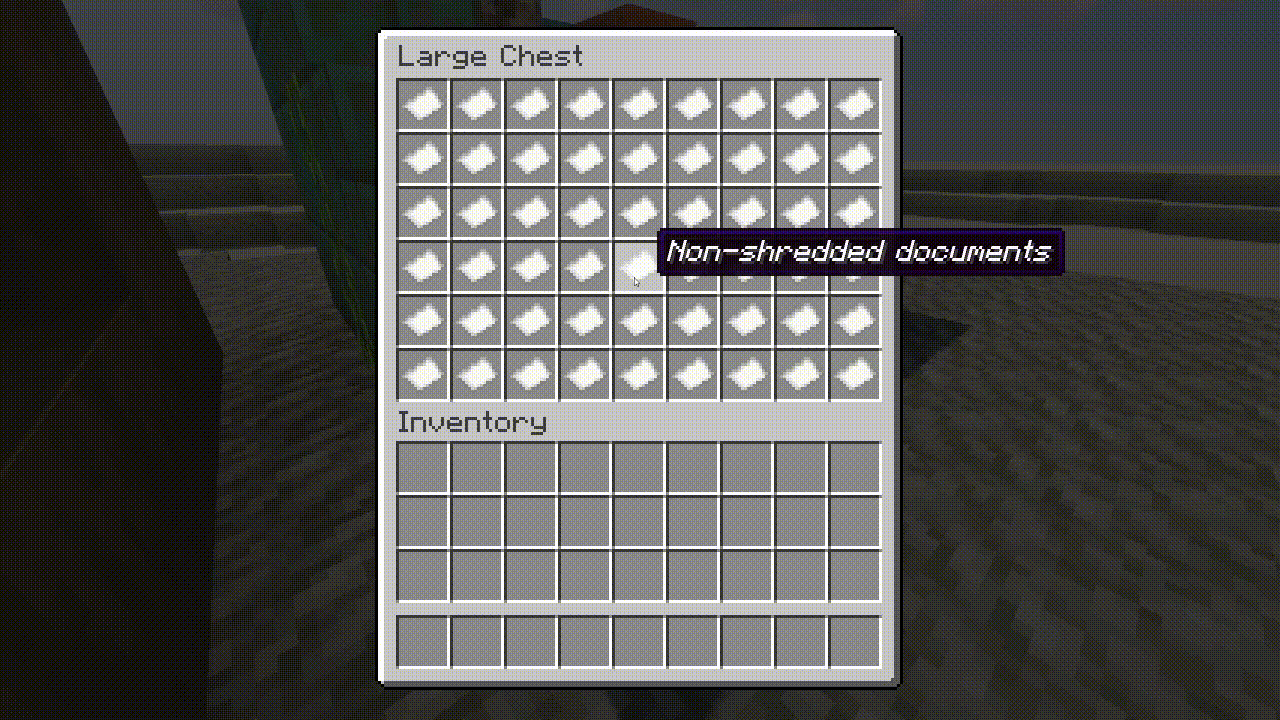

“We tried to incorporate every kind of cyber and operational security problem you may run into when working for a client,” said Salcedo. “We’ve tried to include, virtually, as many different problems and security risks that we’ve actually seen in restaurants or in small businesses in this simulation.”
The simulation recreates a business owner’s office, visualized as Mr. Krabs office, complete with computers, smartphones, and tablets functioning as the point-of-sale system. Users can interact with these devices to evaluate their cybersecurity practices and identify any potential vulnerabilities.



“Many [security] vulnerabilities have to do with the client’s computer, how they’re managing their passwords, what they’re doing with old devices, or where they’re storing important documents or financial documents on [business] premises.”
The co-founders also plugged the UNLVs clinic’s cybersecurity podcast called, “Cyber Clinic Central”, with episodes available on Spotify. The podcast welcomes industry speakers to talk about their career paths as well as welcomes clinic members on to discuss a range of cybersecurity concepts.
After the presentation, students engaged in further group discussions before CLTC concluded the session with the unveiling of this semester’s new “Clinic of Clinics” challenge coin design—colored a vibrant “cyber yellow”! Students can collect a new coin for each “Clinic of Clinics” they participate in.
CLTC thanks all those who participated in the session! For more information about UNLV’s Cyber Clinic, visit freecyberclinic.org or email info@cyberclinicoffical.org


